Cloud:IaaS:3CX: Difference between revisions
From VTX Public Wiki
m (→Configuration of the 3CX system: updated URL of the 3CX web installer + typo correction) |
m (→Preparing the VM: Hided the last bytes of the public IPs) |
||
| Line 82: | Line 82: | ||
* Create the SNAT & DNAT rules on the Edge Gateway (you can use this [[Cloud:Business_Cloud_(IaaS)#Create_a_Firewall_rule_on_Edge|guide]] if needed): |
* Create the SNAT & DNAT rules on the Edge Gateway (you can use this [[Cloud:Business_Cloud_(IaaS)#Create_a_Firewall_rule_on_Edge|guide]] if needed): |
||
In this example, '''"10.10.0.10" is the local IP''' of the 3CX Debian VM and '''"212.40. |
In this example, '''"10.10.0.10" is the local IP''' of the 3CX Debian VM and '''"212.40.XX.XX" is the public IP''' used.<br> |
||
SNAT - Applied on : Edge - Original IP : 10.10.0.10 - Port: Any - Translated IP: 212.40. |
SNAT - Applied on : Edge - Original IP : 10.10.0.10 - Port: Any - Translated IP: 212.40.XX.XX - Port: Any - Protocal : Any - Enable : YES<br> |
||
DNAT - Applied on : Edge - Original IP : 212.40. |
DNAT - Applied on : Edge - Original IP : 212.40.XX.XX - Port: Any - Translated IP: 10.10.0.10 - Port: Any - Protocal : Any - Enable : YES<br> |
||
[[File:FW Edge NATRules VoIP.png|1000px|none]] |
[[File:FW Edge NATRules VoIP.png|1000px|none]] |
||
| Line 91: | Line 91: | ||
* Create the Firewall rules for all VoIP services: |
* Create the Firewall rules for all VoIP services: |
||
''In this example, '''"212.40. |
''In this example, '''"212.40.XX.XX" is the public IP''' used for the 3CX. '''''"vnic1"'' is the virtual interface''' of the 3CX vm.''<br> |
||
{| class="wikitable" |
{| class="wikitable" |
||
| Line 105: | Line 105: | ||
| User |
| User |
||
| Any |
| Any |
||
| 212.40. |
| 212.40.XX.XX |
||
| tcp:5060:any<br />tcp:5061:any<br />udp:5060:any<br /> |
| tcp:5060:any<br />tcp:5061:any<br />udp:5060:any<br /> |
||
| Accept |
| Accept |
||
| Line 112: | Line 112: | ||
| User |
| User |
||
| Any |
| Any |
||
| 212.40. |
| 212.40.XX.XX |
||
| tcp:5090:any<br />udp:5090:any<br /> |
| tcp:5090:any<br />udp:5090:any<br /> |
||
| Accept |
| Accept |
||
| Line 119: | Line 119: | ||
| User |
| User |
||
| Any |
| Any |
||
| 212.40. |
| 212.40.XX.XX |
||
| tcp:443:any<br />tcp:5001:any<br /> |
| tcp:443:any<br />tcp:5001:any<br /> |
||
| Accept |
| Accept |
||
| Line 126: | Line 126: | ||
| User |
| User |
||
| Any |
| Any |
||
| 212.40. |
| 212.40.XX.XX |
||
| udp:9000-10999:any<br /> |
| udp:9000-10999:any<br /> |
||
| Accept |
| Accept |
||
| Line 133: | Line 133: | ||
| User |
| User |
||
| Any |
| Any |
||
| 212.40. |
| 212.40.XX.XX |
||
| tcp:5015:any |
| tcp:5015:any |
||
| Accept |
| Accept |
||
Revision as of 14:14, 11 November 2021
Introduction[edit | edit source]
The goal of this page is to be able to setup a 3CX PBX system hosted in our VTX IaaS infrastructure.
Presentation of the Product[edit | edit source]
FIXME: To be written with PM
Prerequisites[edit | edit source]
- Have subscribed to a "Connect_PABX-IP*" service at VTX.
- Have subscribed to a "Business Cloud-IaaS" service at VTX.
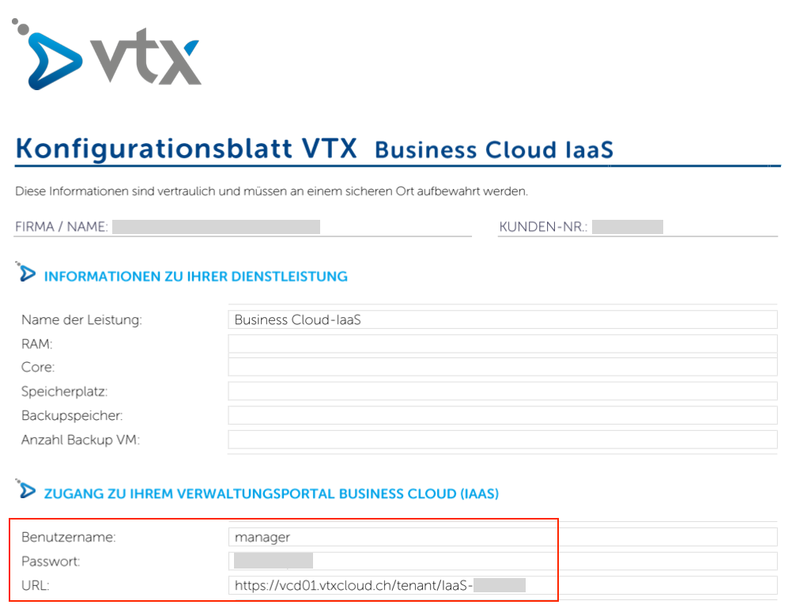
- Have downloaded the "configsheet" PDF file who contains the "Business Cloud-IaaS" credentials.
- If the option with "Edge Gateway" has been ordered, define a private network subnet (Wikipedia.org - Private IPv4 addresses).
- Choose a size of "VM Sizing Policy" according to your needs using the chart below:
| Size of the organization | Requirements | VM Sizing Policy |
|---|---|---|
| Small (up to 10 ext.) | 1vCPU - 1GB RAM - 30GB Storage | Small 3CX |
| Medium (up to 50 ext.) | 4vCPU - 4GB RAM - 100GB Storage | Medium 3CX |
| Large (up to 250 ext.) | 6vCPU - 8GB RAM - 300GB Storage | Large 3CX |
Retrieve the credentials of the "Business Cloud-IaaS" service[edit | edit source]
First you have to connect to the VTX Kiosk : https://kiosk.vtx.ch.
- Click on "Mes Services"/"Meine Dienste"
- Then click on "Mes feuilles de configuration"/"Meine Konfigurationsblätter"
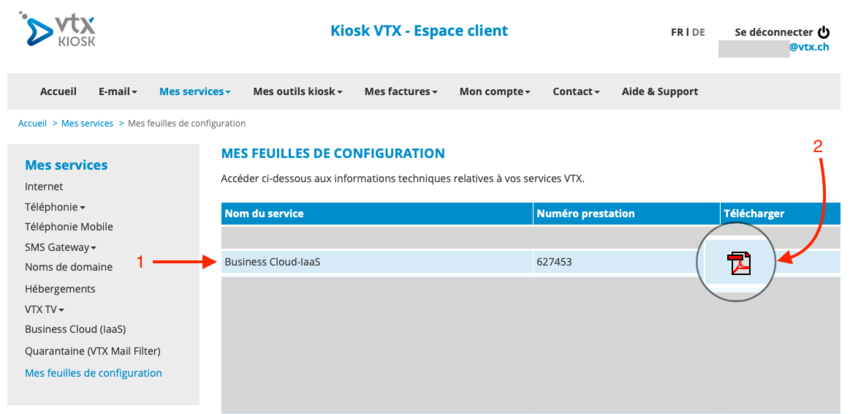
- Search for the right service "Business Cloud-IaaS".
- Click on the PDF icon in the right to download it.
Then open this file. You can found the credentials there :
Preparing the VM[edit | edit source]
Connect to the URL of your vtxcloud.ch account (ex. : https://vcd01.vtxcloud.ch/tenant/XXXXXX/) and follow all steps of section "Creating the first VM step-by-step" by using these settings :
- For Type : New.
- For OS family : Linux.
- For Operating System : Debian GNU/Linux 10 (64-bit).
- For Boot image : debian-amd64-netinst-3cx.iso.
- For Sizing Policy : Use the chart from Cloud:IaaS:3CX#Prerequisites to choose the good VM Sizing Policy fitting your needs.
- For Storage : Choose "IaaS SSD" and use the chart from Cloud:IaaS:3CX#Prerequisites to know requirements in terms of storage size (30GB/100GB/300GB) matching your VM Sizing Policy.
- For Network Configuration :
Without Edge firewall
You can directly setup the VM with a public IP. The VM will be secured by the integrated firewall named "NFtables".
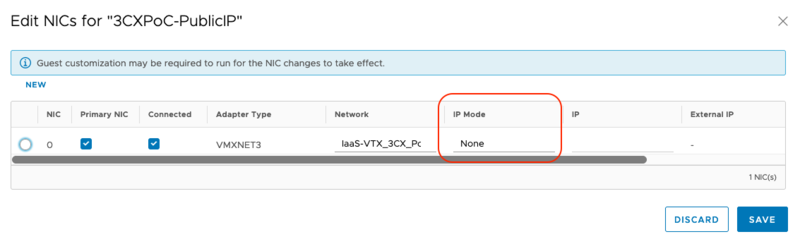
You need to edit the NIC setting by clicking in the "Details" button of your VM. Then under "Hardware", click on "NICs" and "Edit".
In the "IP Mode" choose "None" and then "Save".
With Edge firewall
- Be sure that there is no DHCP activated on the network of your VM to avoid IP config issues.
- Create a new internal network: Network Type: Routed. Interface Type: Internal. You can use this guide if needed.
- Edit the NIC of you virtual machine and attach it to the newly created private network. You can use this guide if needed.
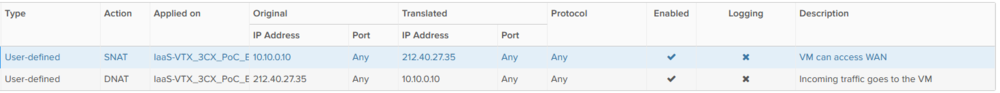
- Create the SNAT & DNAT rules on the Edge Gateway (you can use this guide if needed):
In this example, "10.10.0.10" is the local IP of the 3CX Debian VM and "212.40.XX.XX" is the public IP used.
SNAT - Applied on : Edge - Original IP : 10.10.0.10 - Port: Any - Translated IP: 212.40.XX.XX - Port: Any - Protocal : Any - Enable : YES
DNAT - Applied on : Edge - Original IP : 212.40.XX.XX - Port: Any - Translated IP: 10.10.0.10 - Port: Any - Protocal : Any - Enable : YES
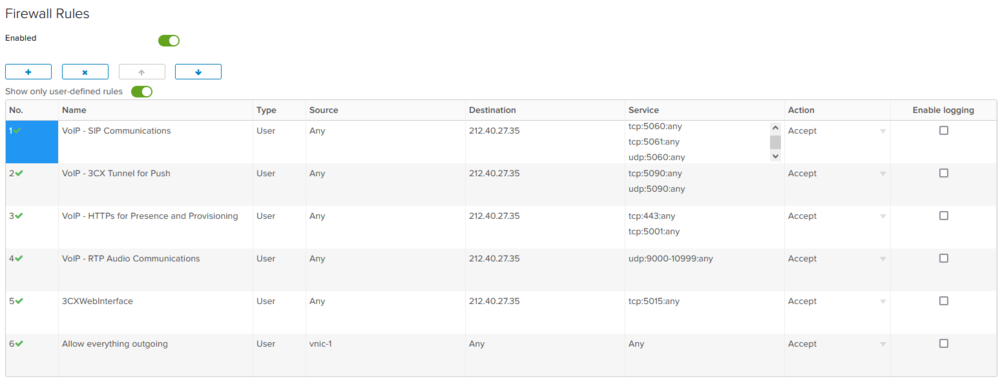
- Create the Firewall rules for all VoIP services:
In this example, "212.40.XX.XX" is the public IP used for the 3CX. "vnic1" is the virtual interface of the 3CX vm.
| Name | Type | Source | Destination | Service | Action |
|---|---|---|---|---|---|
| VoIP - SIP Communications | User | Any | 212.40.XX.XX | tcp:5060:any tcp:5061:any udp:5060:any |
Accept |
| VoIP - 3CX Tunnel for Push | User | Any | 212.40.XX.XX | tcp:5090:any udp:5090:any |
Accept |
| VoIP - HTTPs for Presence and Provisioning | User | Any | 212.40.XX.XX | tcp:443:any tcp:5001:any |
Accept |
| VoIP - RTP Audio Communications | User | Any | 212.40.XX.XX | udp:9000-10999:any |
Accept |
| 3CX Web Interface | User | Any | 212.40.XX.XX | tcp:5015:any | Accept |
| Allow everything outgoing | User | vnic-1 | Any | Any | Accept |
You should have this:
Creating the first VM step-by-step[edit | edit source]
To create a VM, go to your vDC then click on the New VM link
- Name: Choose a name for your VM on vCloud Director
- Computer name: Chose the hostname for your VM. This settings will have no effect on the VM itself if you don't use VMware Tools and don't enable the Guest Optimization.
- Description: Choose a description of your VM
- Type: If you have a VM template you can choose it. If not choose New and uncheck the box Power on.
- OS family: Choose the kernel OS, Windows, Linux or other
- Operating System: Choose the OS and version that you will install
- Boot image: Choose the ISO, if you created a custom library you will be able to see your own ISO
- Select a Size: By default, you can choose some default ressources (Small, Medium, Large) or if needed you can check the Custom Sizing Options case and configure the ressources that you want.
- On the Storage table, choose the IaaS SSD on the Storage Policy column then choose the SSD
- On the Networking table, choose your internal network created previously.
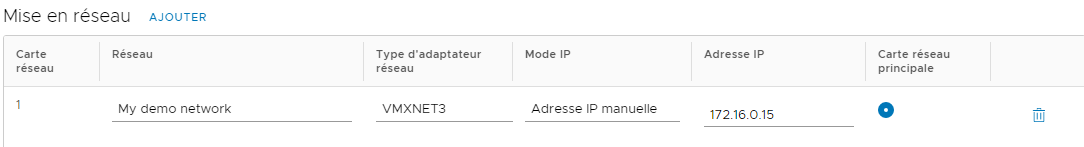
- IP Mode: You can choose for example Manual IP to assign the VM a static IP manually. Select Static IP Pool to assign the VM the next available IP from the previously configure Static IP Pool. This settings will have no effect on the VM if you don't use VMware Tools and don't enable the Guest Optimization.
- When all settings has been done, click on the OK button, VM will be created in few seconds.
Network configuration:
Connecting VMs to external network with outgoing NAT rule
By default access to the public internet is blocked. You'll need to create a SNAT rule to enable internet access for your VMs.
Go to Edges, select your Edge gateway and click to the Services link then click on the NAT tab.
- Click on the + SNAT Rule button
- Applied On: Select our Edge gateway
- Original Source IP/Range: Select the local IP of your VM
- Translated Source IP/Range: Click on the Select button, you should be able to choose one of our public IP provided by VTX
- Destination IP Address: Put any
- Destination Port: Put any
- Description: If needed you can choose a description
By default the rule will be enabled by the toggle button Enabled, if you want you can enable the log with toggle button Enable logging. When is done, you can create the rule by clicking on the Keep button.
When the rule is created, click on the Save changes link at the top right of the screen, it will reload the Edge rule to apply the new configuration.
3CX Installation using custom 3CX Debian ISO[edit | edit source]
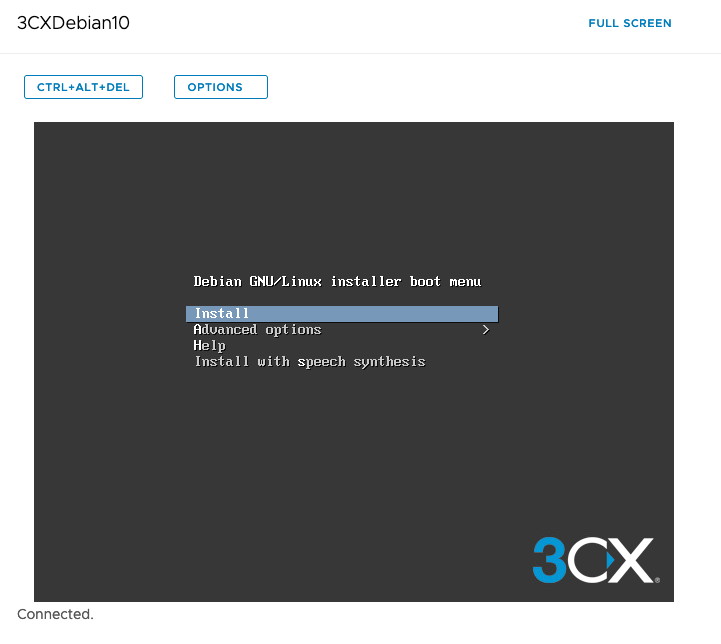
Boot your VM via the vCloud panel : "Actions" -> "Power On"
Press Enter when you are on « Install »
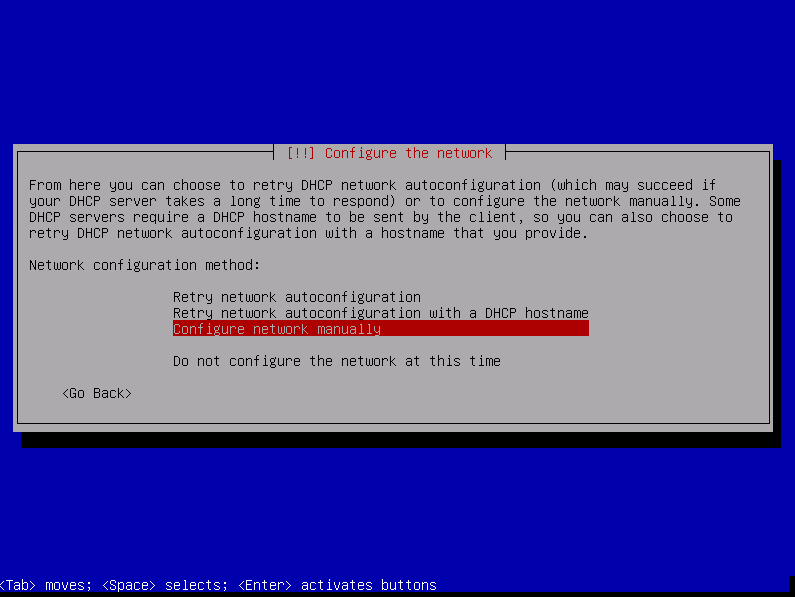
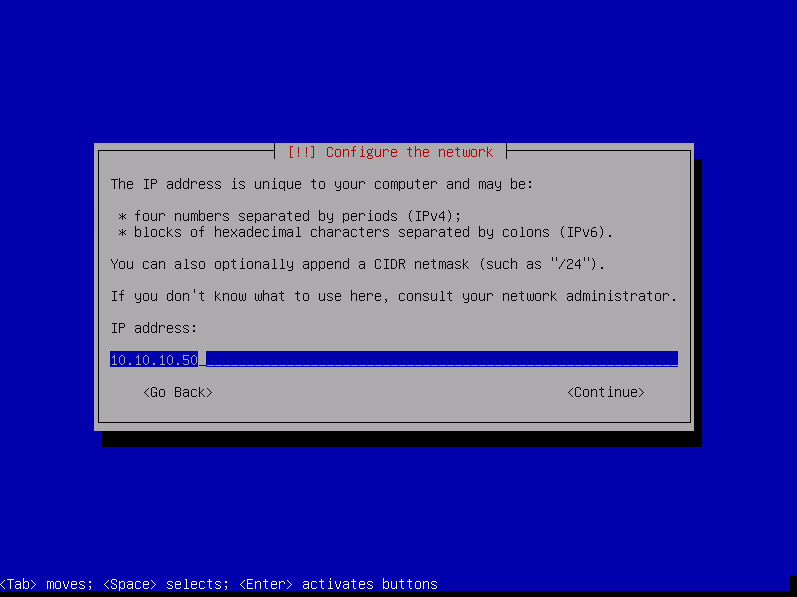
First you will start with the network configuration. In our case we will select « Configure network manually »
Enter the IP then select « Continue » and press enter.
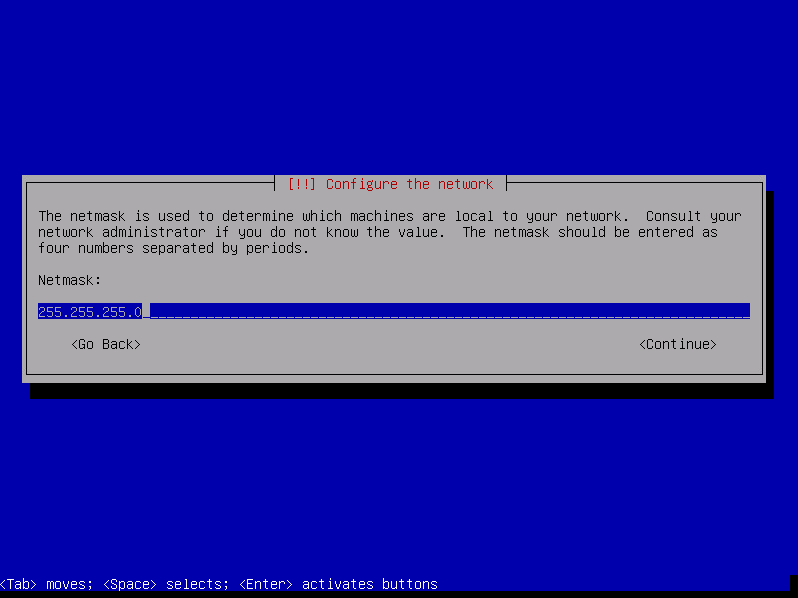
Fill netmask then select « Continue » and press enter.
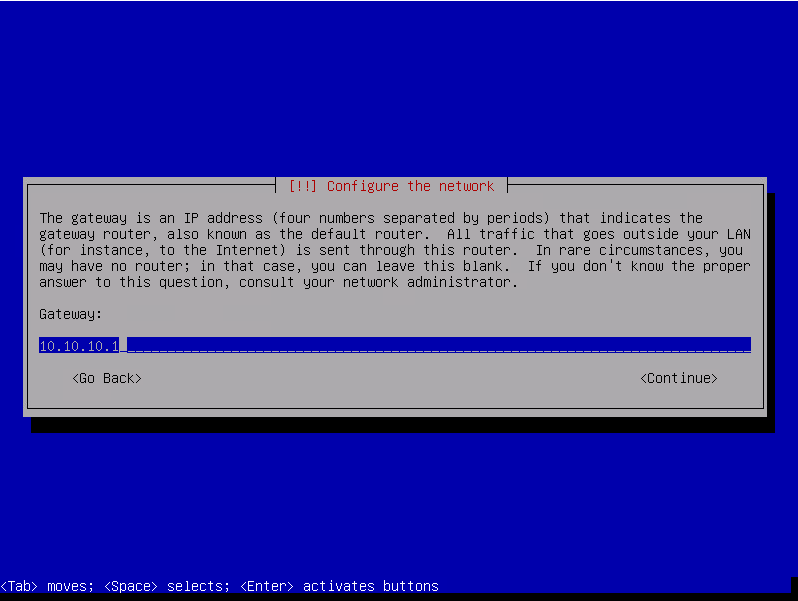
Fill gateway then select « Continue » and press enter.
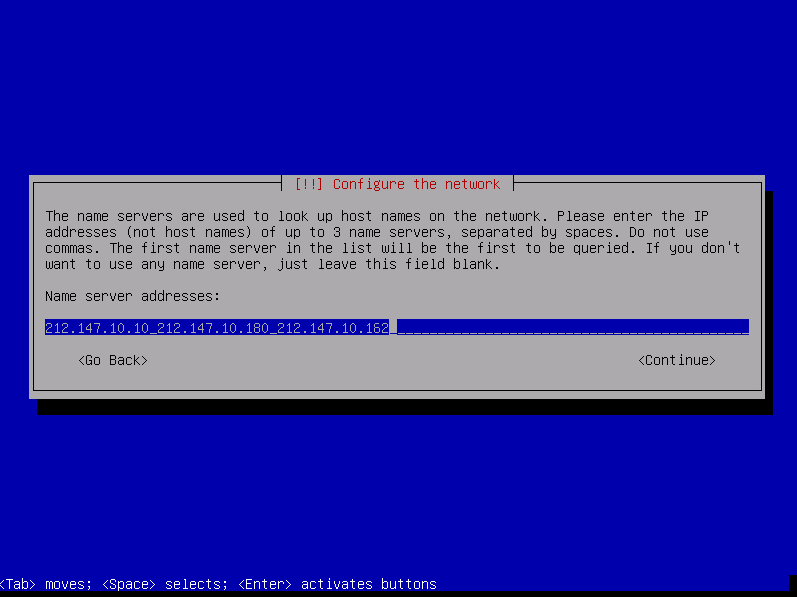
Fill name server addresses then select « Continue » and press enter.
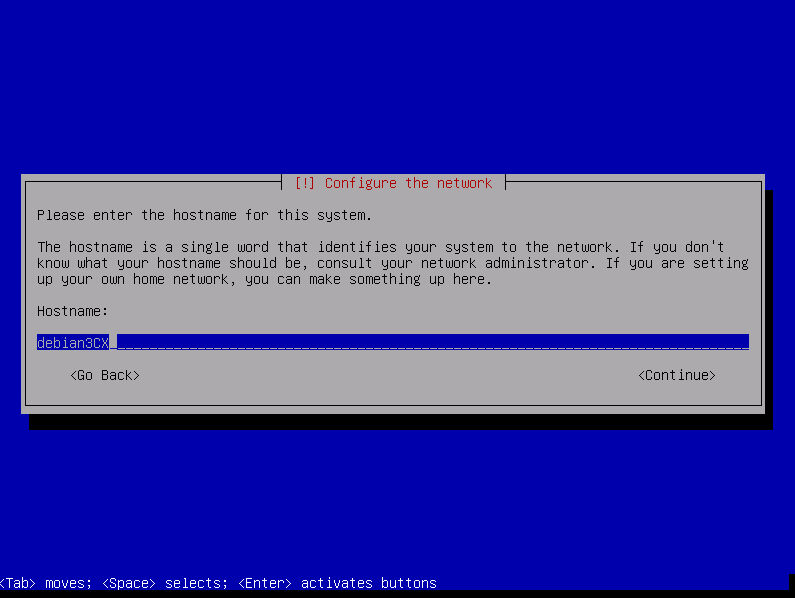
Fill hostname then select « Continue » and press enter.
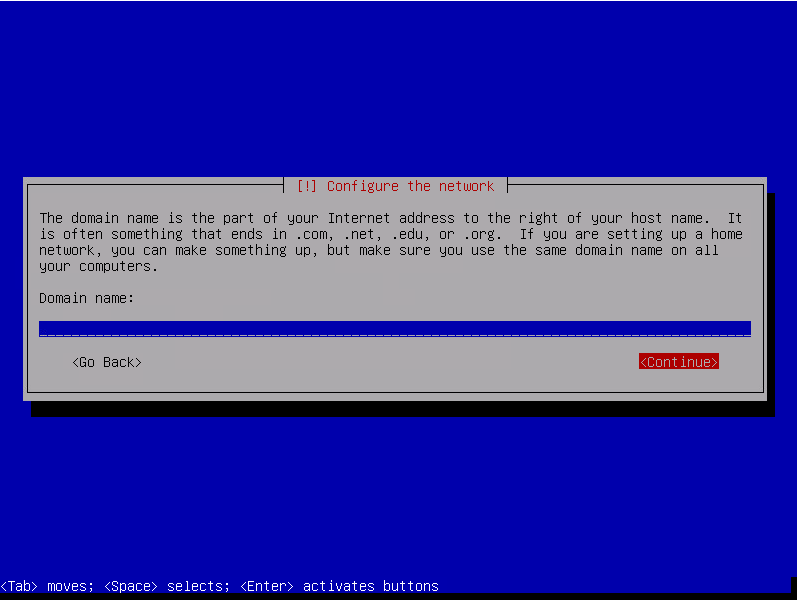
Fill domain name then select « Continue » and press enter.
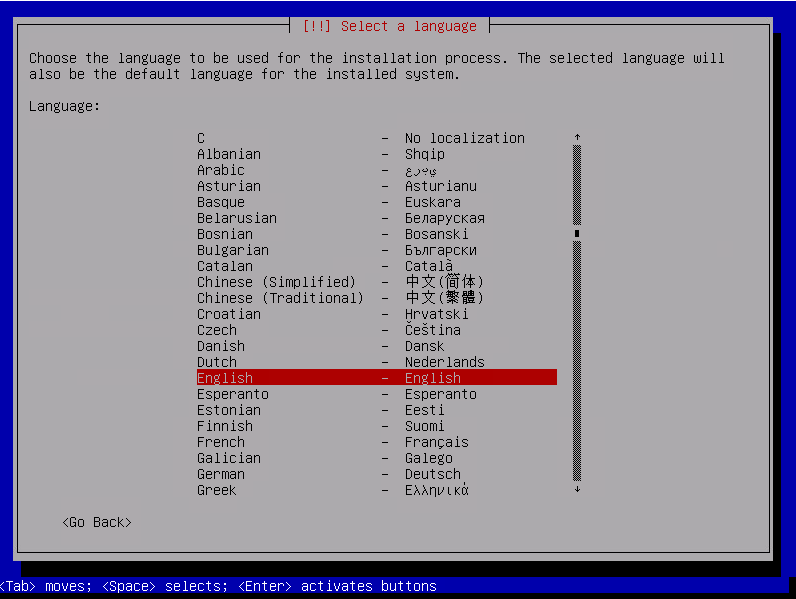
Choose language and press enter.
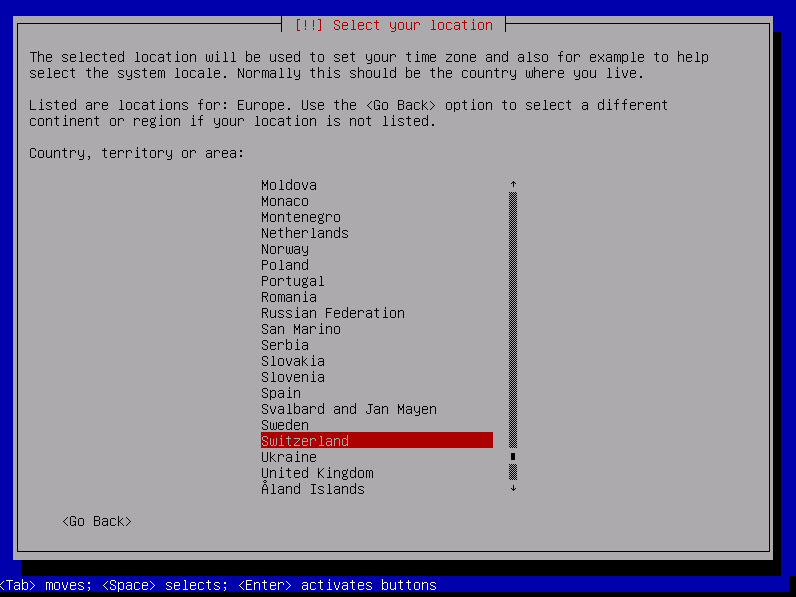
Choose the location, go to « other », « Europe » then « Switzerland »
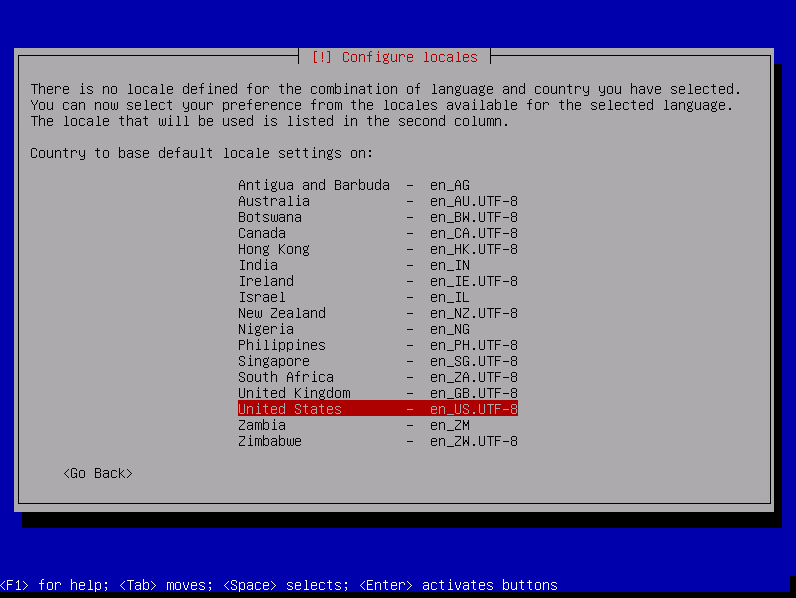
Choose your locales, by default en_US.UTF-8
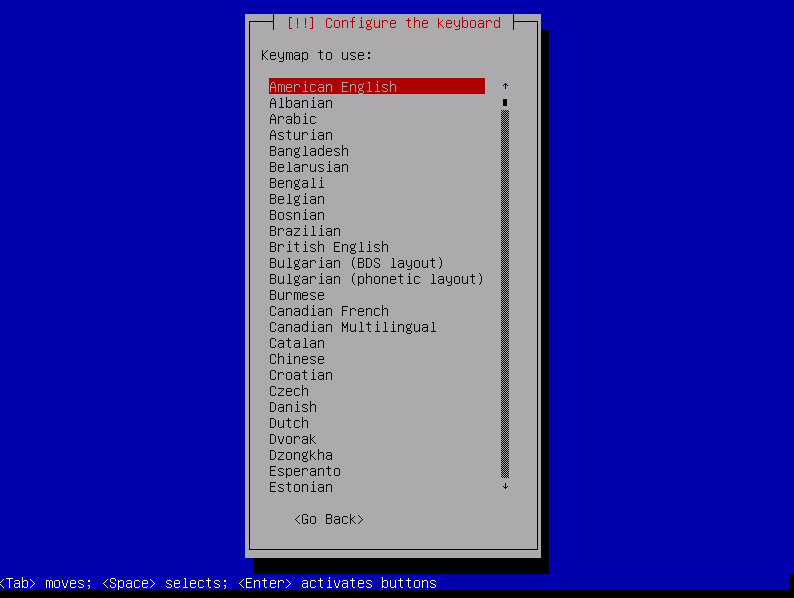
Choose your keyboard layout, in our case « Swiss french ».
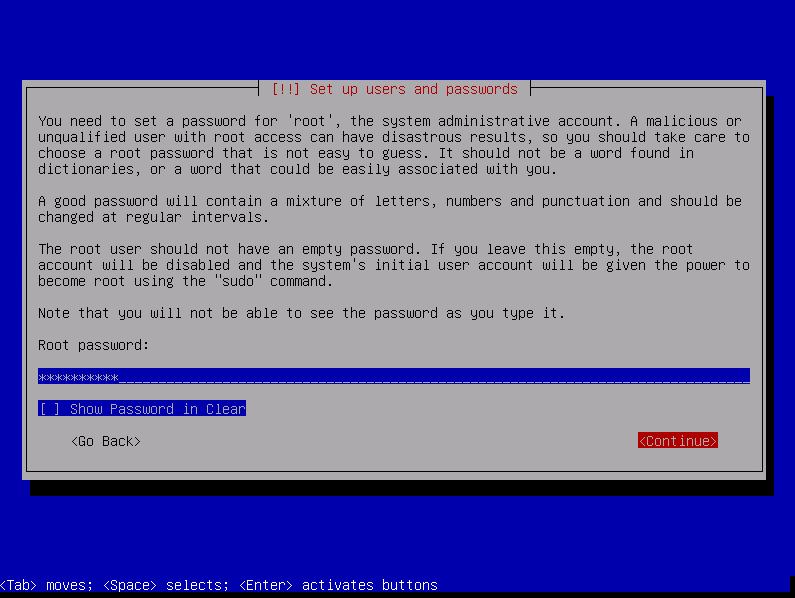
Create the root password
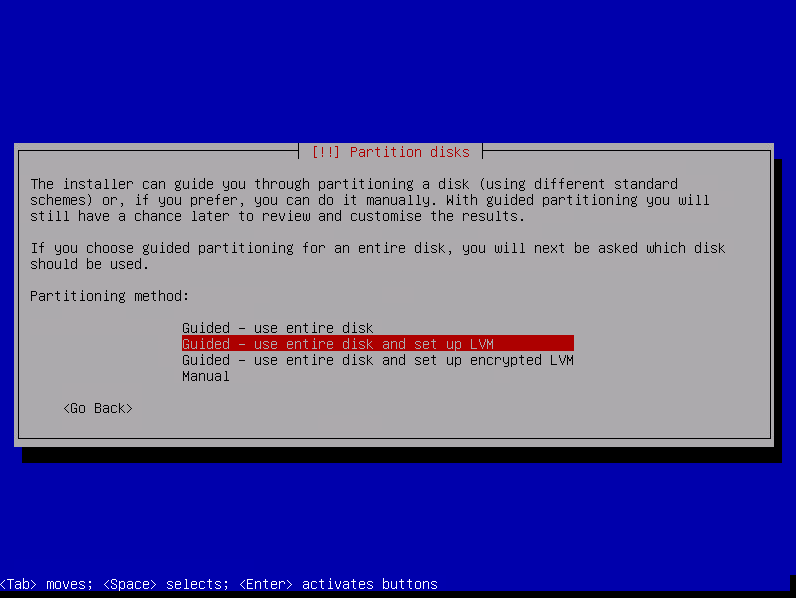
Choose partitioning method, we will choose « Guided - use entire disk and set up LVM »
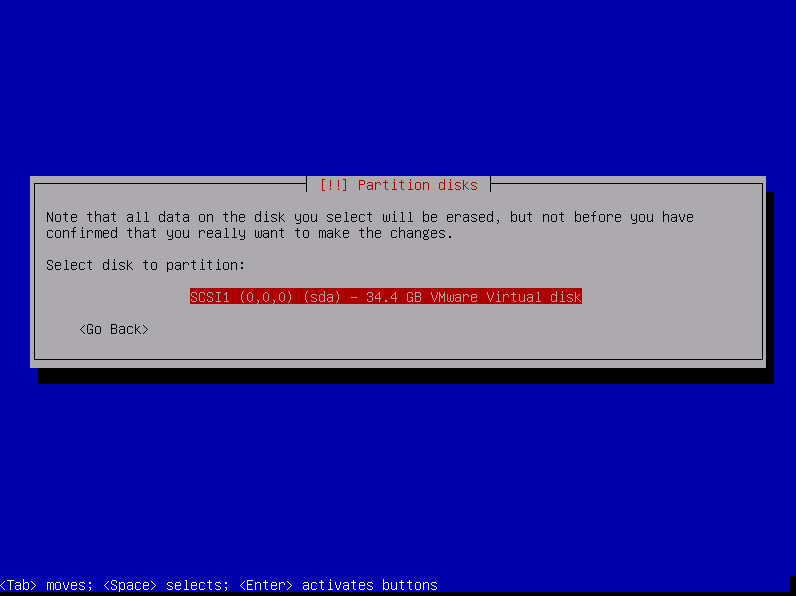
Select the disk to partition then press enter.
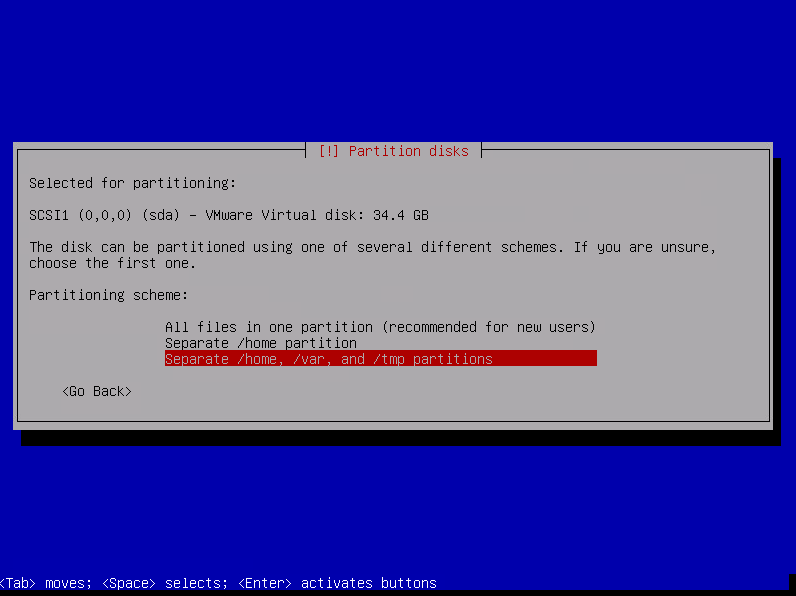
Choose the partitioning scheme « Separate /home, /var, and /tmp partitions » and press enter
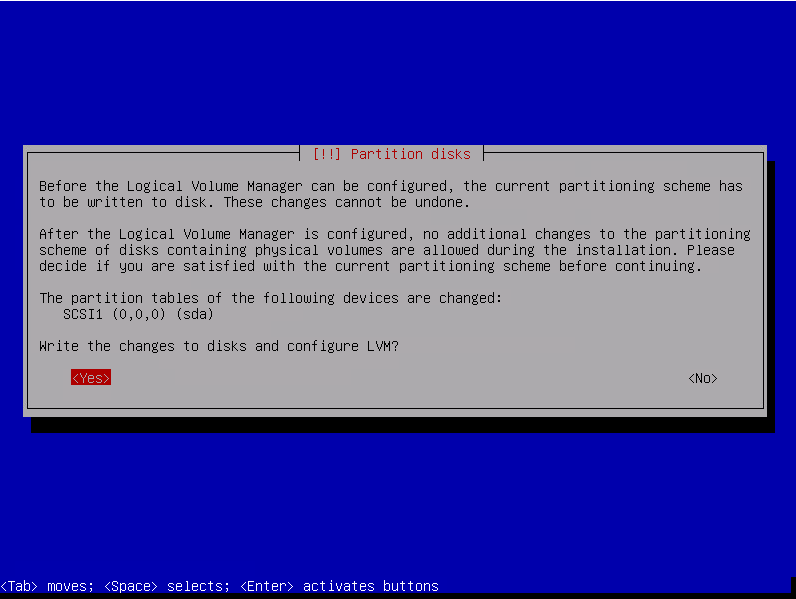
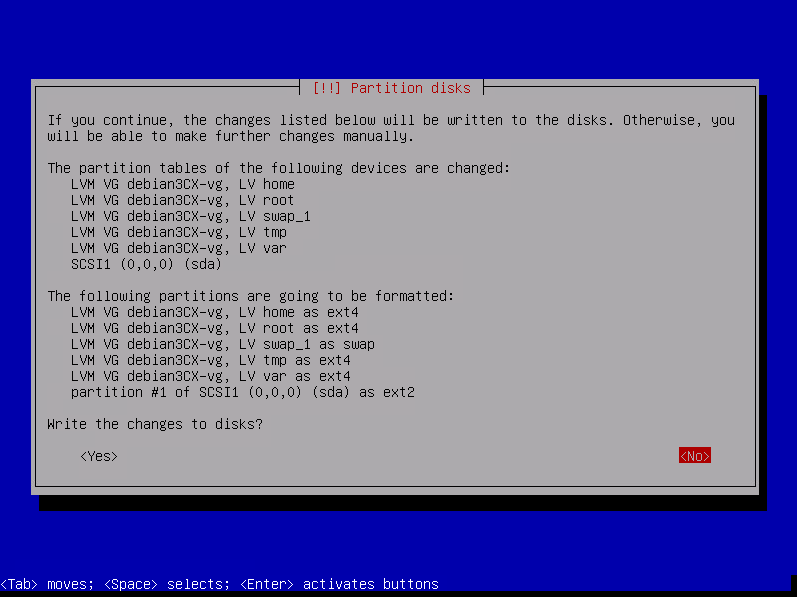
Select YES to write changes to disks and confirm with enter
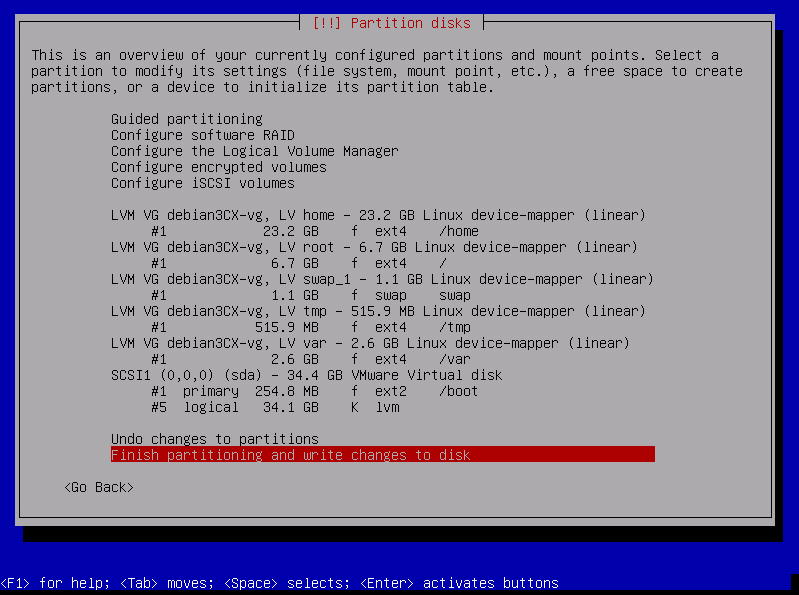
Review the partitioning then select « Finish partitioning and write changes to disk » then press enter
Confirm the writes by selecting « YES » then press enter
The system will install all components then reboot automaticaly.
Configuration[edit | edit source]
Configuration of the 3CX system[edit | edit source]
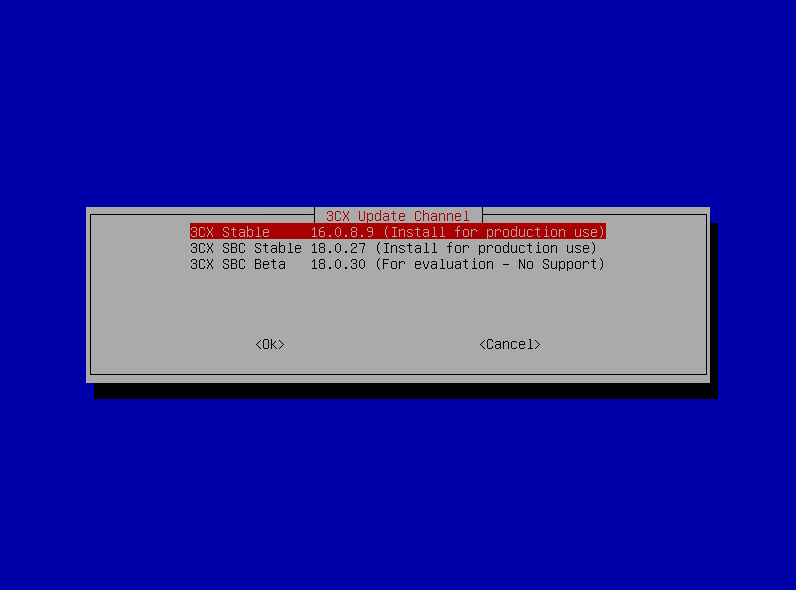
After the reboot you will need to select « 3CX Stable X.X.X.X (Install for production use) and press enter
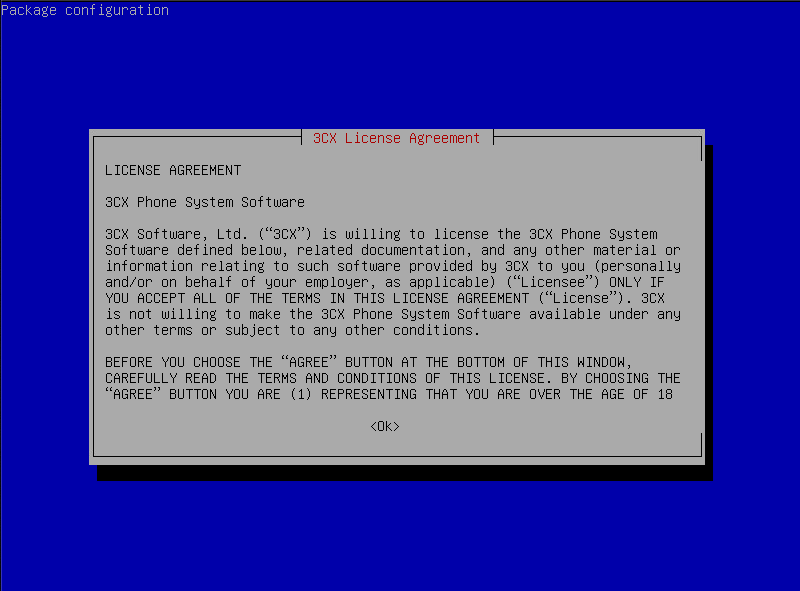
After installation you need to accept the 3CX License Agreement.
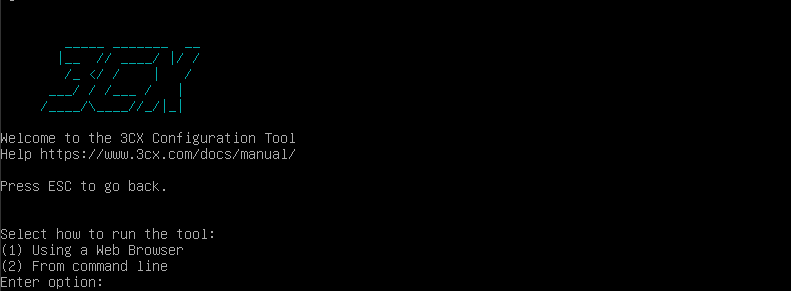
After that the system will reboot into 3CX Configuration Tool.
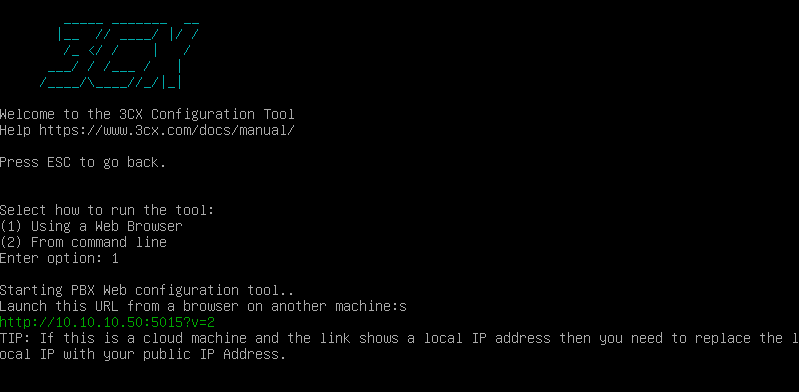
Choose option "1"
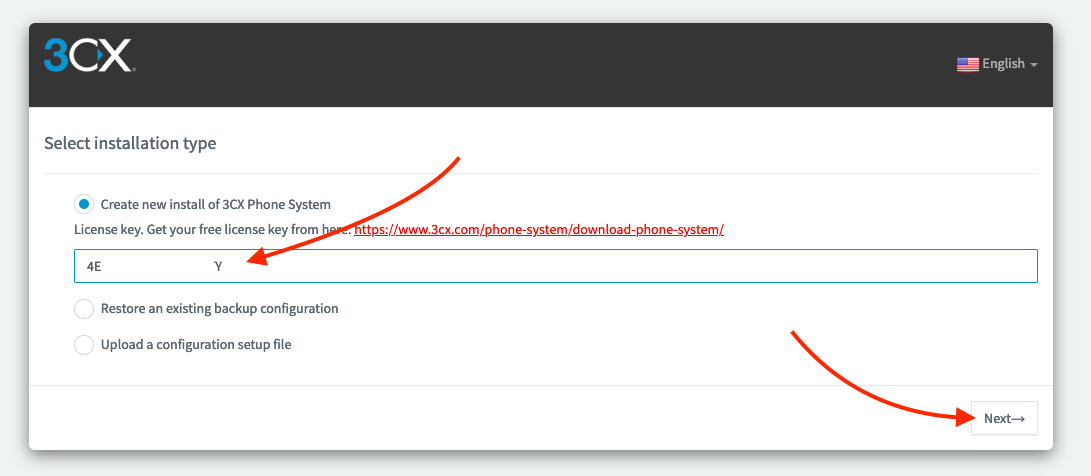
Go to the webpage http://YOURIP:5015 Then choose the installation type. In our case « Create new install of 3CX Phone System ». Enter the license key then click « Next ».
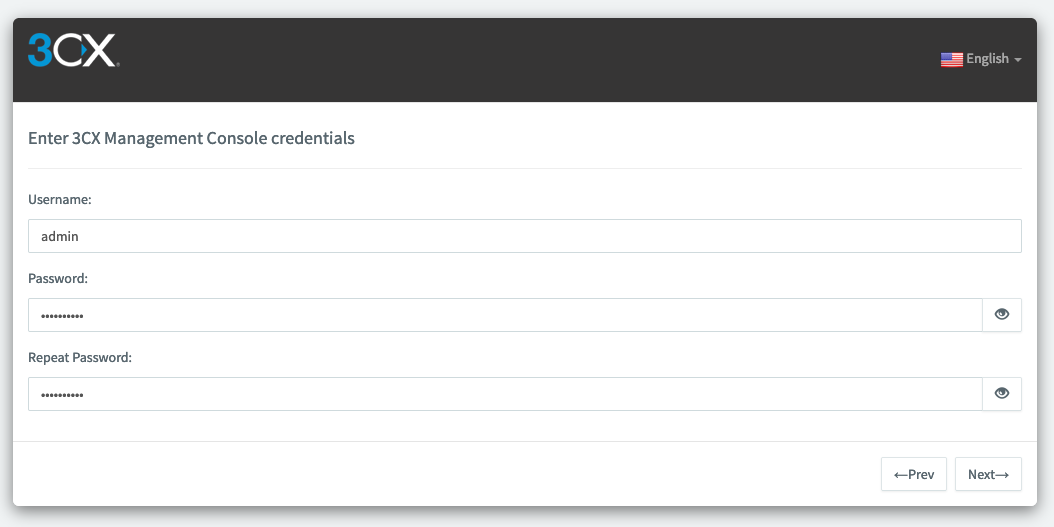
Then create the credentials for your 3CX Management Console then click on « Next »
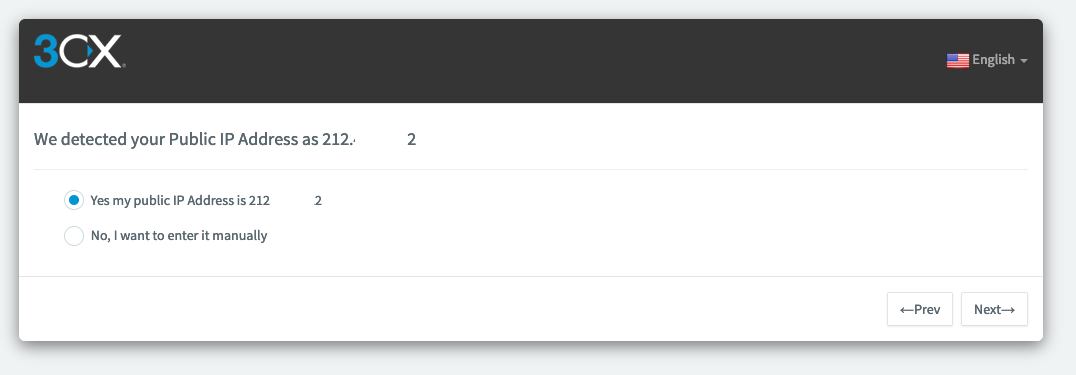
Then the tool will detect your public IP (if it is not correct choose « No, i want to enter it manually ») then click on « Next »
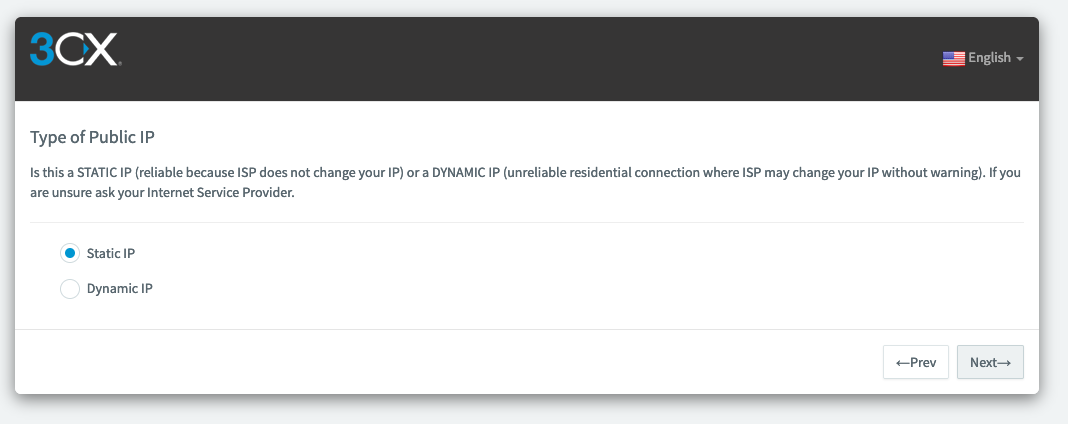
Then choose your type of Public IP and click on « Next »
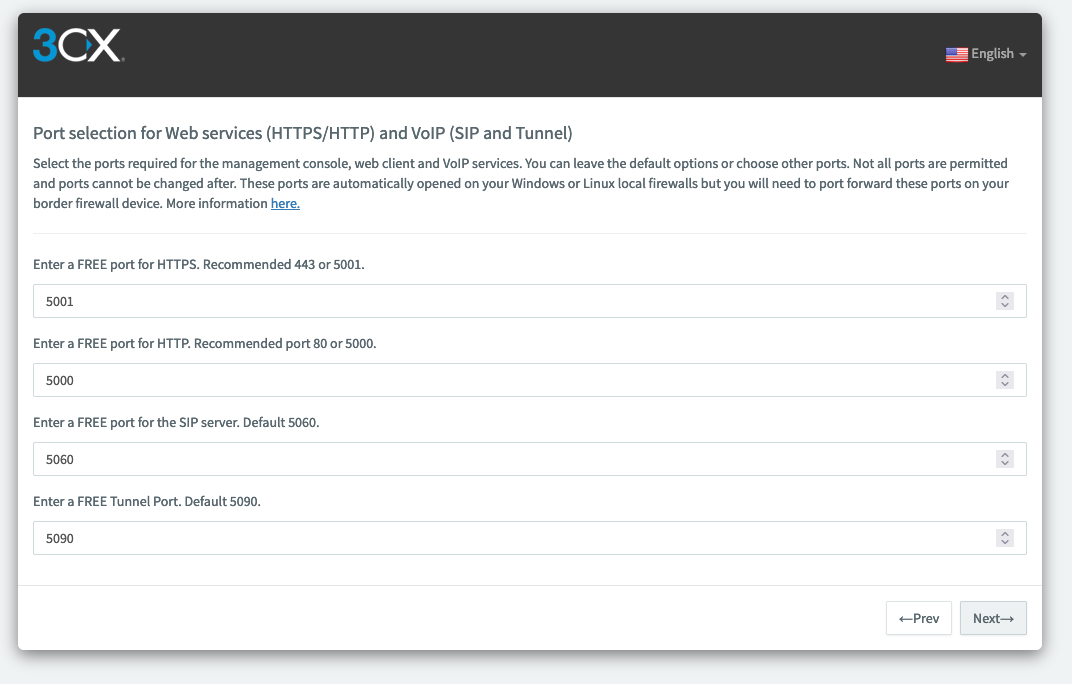
Then let by default all ports configuration
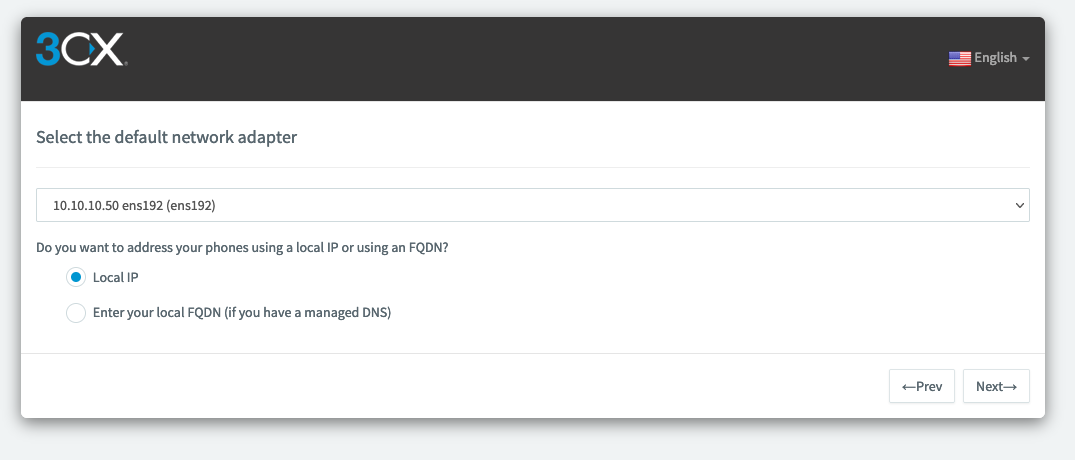
Select the right network adapter
Wait until everything is automatically configured.
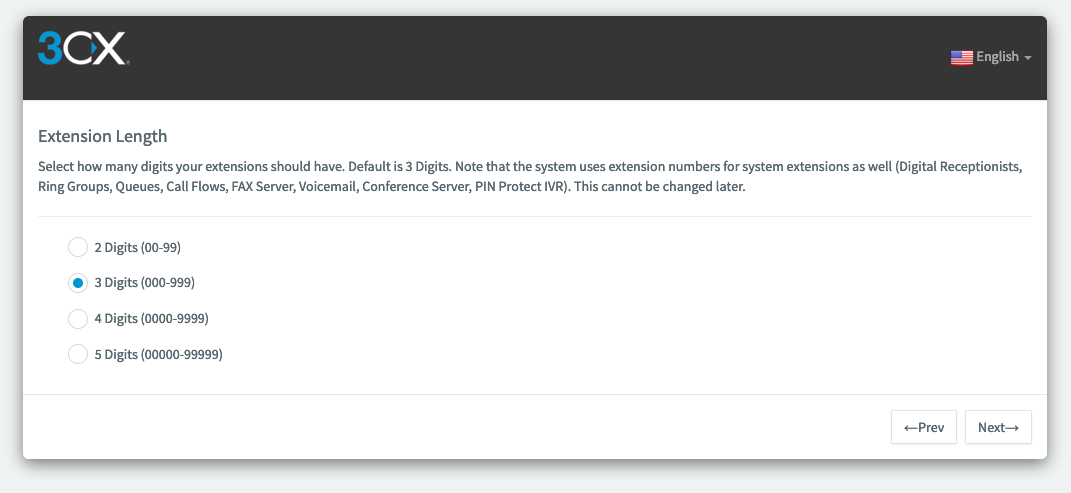
Choose the extension length, in our case "3 Digits"
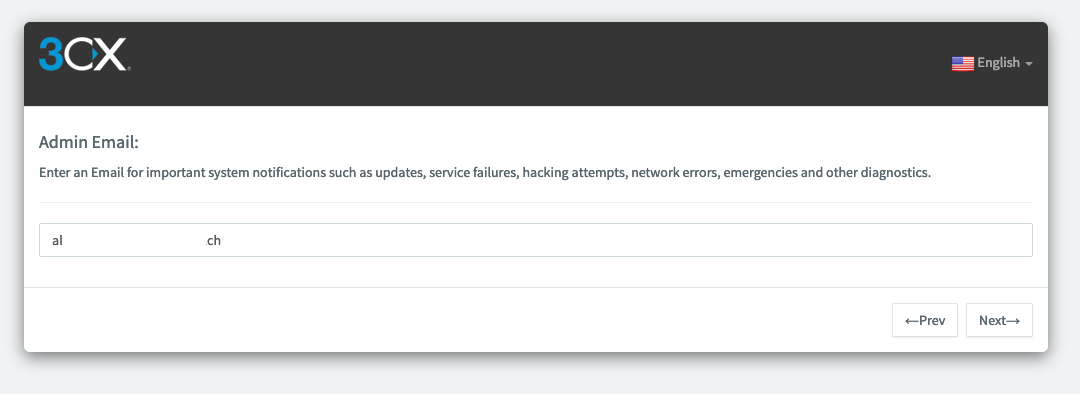
Then enter your admin email address and click on « Next »
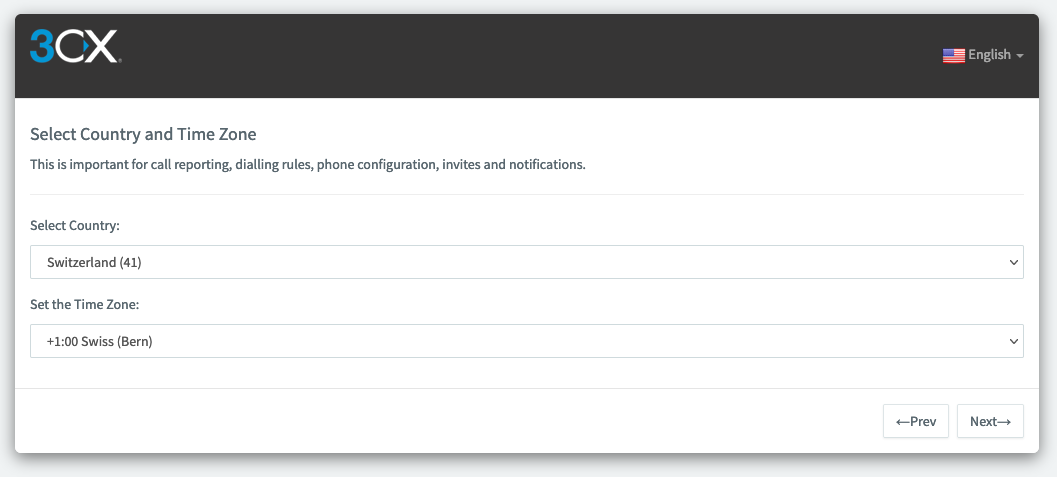
Choose your Country and Time Zone then click on « Next »
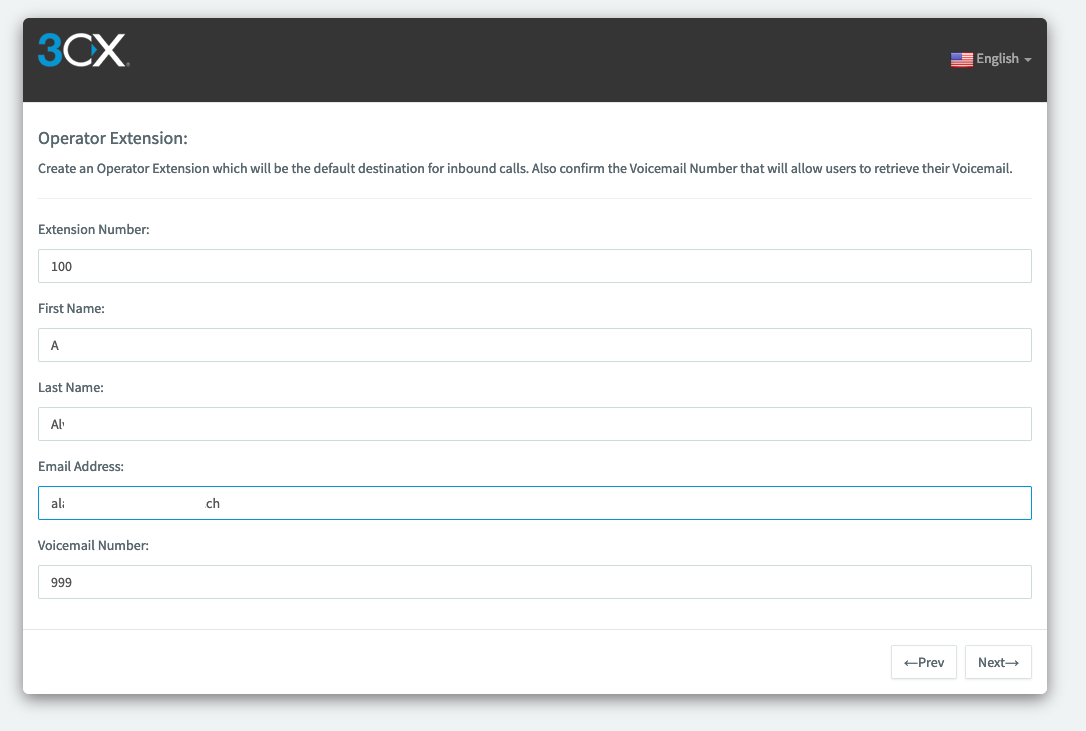
Create the Operator extension
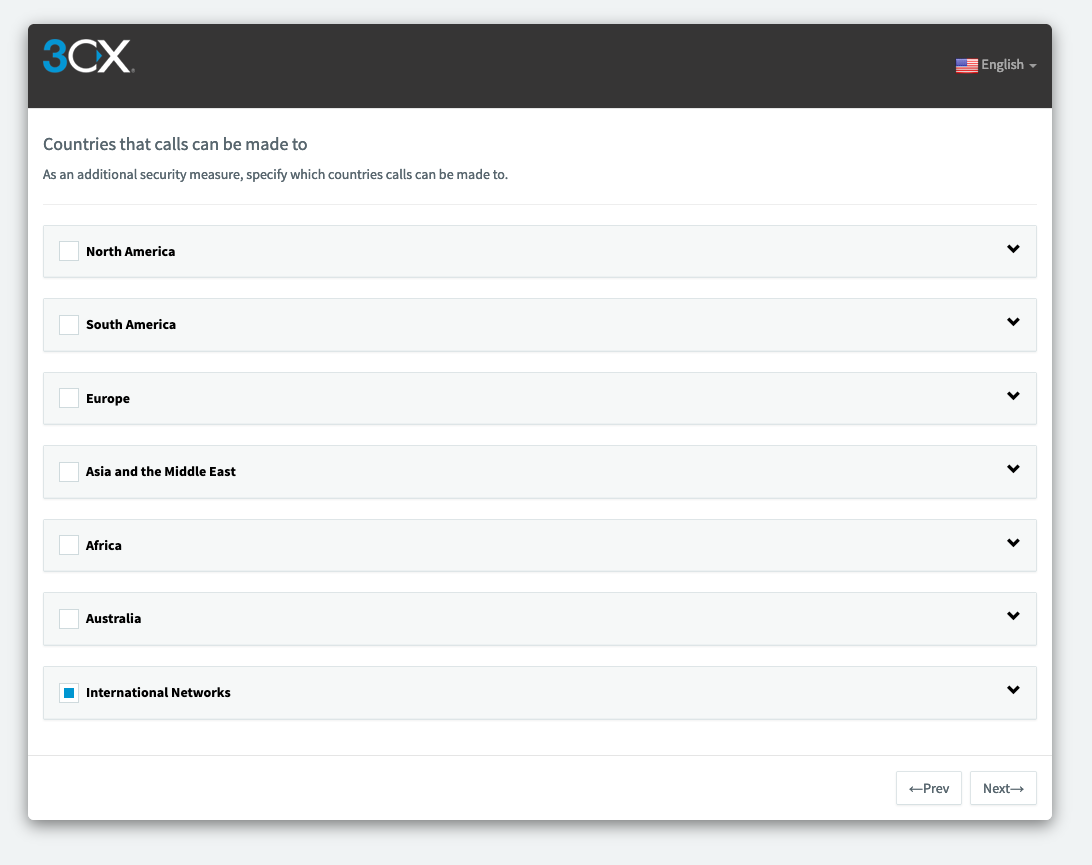
Choose « International Networks » then click on « Next »
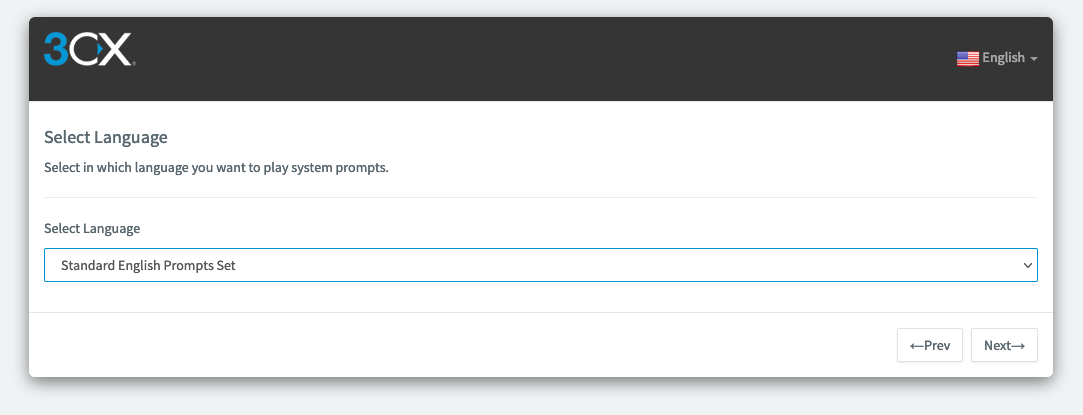
Select the language of the trunk.
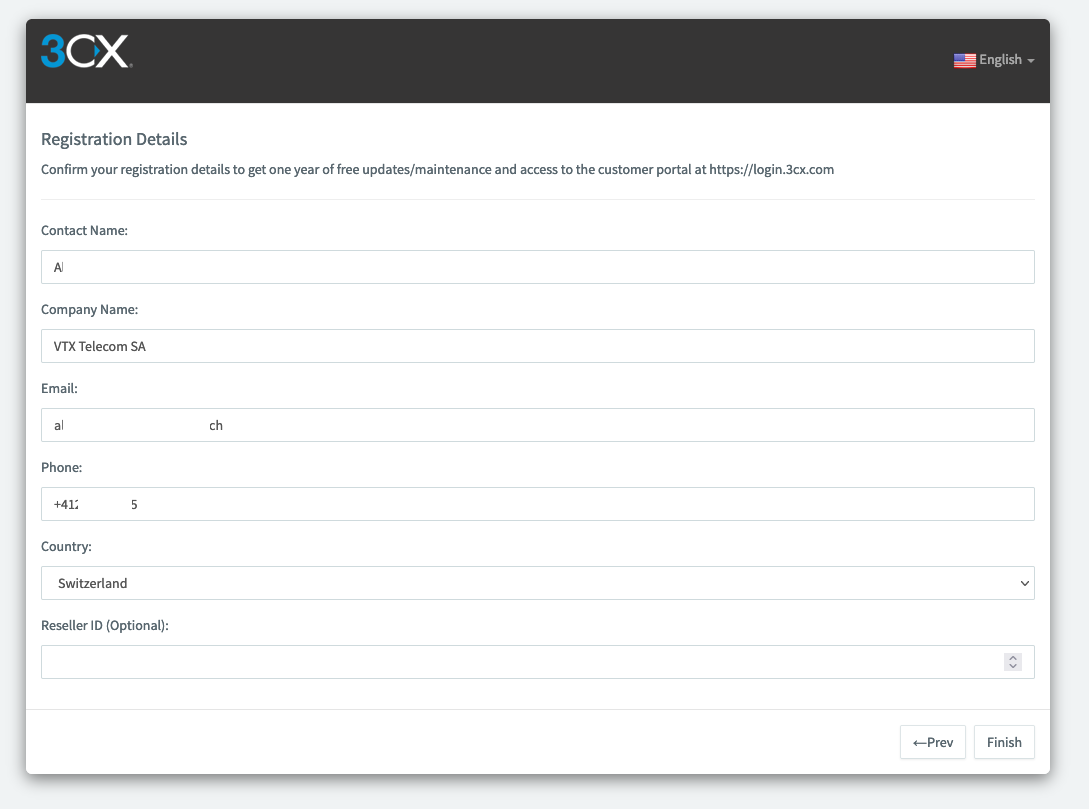
Confirm the registration details at 3CX and click « Finish »
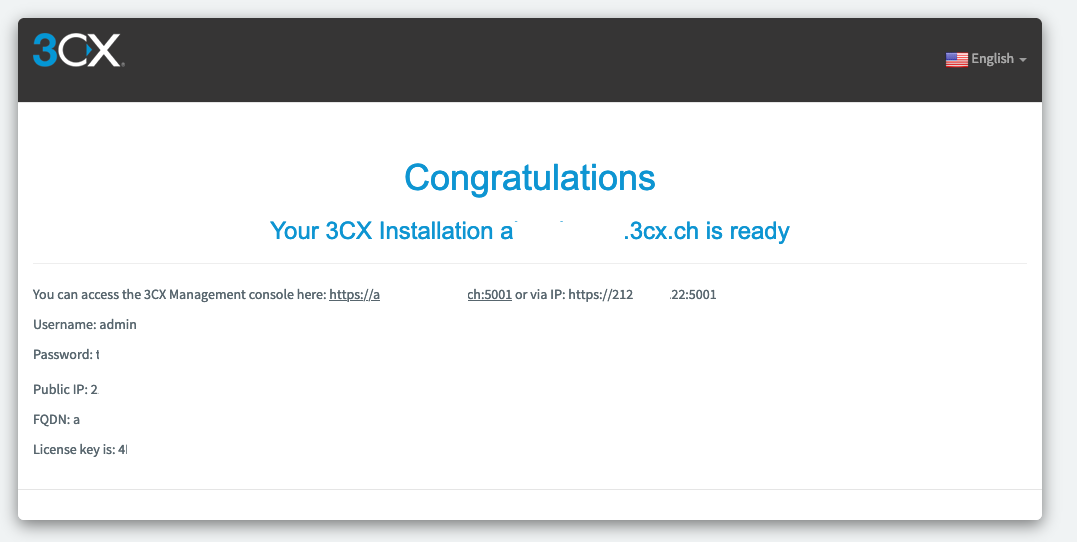
Then you will see this confirmation of the 3CX installation with all useful information
Setup 3CX Trunk using VTX SIP Trunk Template[edit | edit source]
FIXME: To be added