The purpose of this page is to help partners and customer ITs to setup their firewall without having to guess for our Telephony Platform Access Lists
A Copy of this page is available at https://wiki.vtx.ch/wiki/Network:Firewall:Configuration

|
Please make sure your firewall is running the last stable version of his firmware and is not End Of Life or End Of Support because we coped with many bugs on Zyxel / Sophos / Sonicwall / ... firewalls running old versions
|

|
| SIP ALG: Because many implementations of SIP ALG are not working correctly (bug or incompatibility with some phones), we have configured the VoIP platform to handle NAT all the time. SO PLEASE DO NOT USE "SIP ALG", it is not needed |
| STUN / TURN: Because STUN is not working in call cases (like symmetrical NAT), we have configured the VoIP platform to handle NAT all the time. SO PLEASE DO NOT USE "STUN" nor "TURN", it is not needed |
Firewall NAT and QOS configuration[edit | edit source]
- NAT Timeout: Set the NAT/firewall UDP timeout to a minimum of 30s for SIP/UDP and 600s for SIP/TCP
- QOS: You need to reserve 100kbps per concurrent call and 100 kbps per 10 BLF NOTIFY message (LED blinking in the same time on the phones)
- SIP ALG: To disable ( cf warning above)
- MTU: Please make sure you are using the good MTU value on the LAN and WAN interface of your firewall
- 1500 on the LAN
- 1500 on the WAN if Firewall is only doing routing
- 1492 on the WAN if Firewall is doing PPPoE
| On Sonicwalls, if you have a MTU 1492 on the WAN, please set "Do not send ICMP Fragmentation Needed for outbound packets over the Interface MTU", otherwise it will break calls for snom phones that will display "Network Failure", cf screenshot below |
Network and NAT setup : STUN / TURN / externip / SIP ALG[edit | edit source]
| Please do not set up any NAT detection, no STUN, no TURN, no SIP ALG, no externip ! |
- Problem 1: The usage or STUN or TURN or SIP ALG is useful to perform some peer to peer VoIP communication, but these protocols are not working in 100% of cases ( i.e: when using symmetrical NAT (almost all firewall now), or having a firewall that do not support hairpin or do not allow LAN to LAN communication ( like in Hotel Rooms ) )
- Problem 2: The other problem is that some implementations of these protocols are buggy on some equipments ( phone or PBX or firewall )
- Conclusion: Since these protocols are not working in all cases and are sometimes buggy, the VTX VoIP platform is always handling NAT detection and all VoIP stream goes via the VTX VoIP platform. Consequently, no need to enable these protocols

|
You do not need any incoming firewall rule or NAT rules for your phones to work correctly. You need your firewall to be stateful and allow incoming traffic that have been triggered by an outgoing request. Please follow 1st chapter. ex: phone is REGISTERING on the platform and maintain it each 30s to allow incoming calls to work because the VoIP platform will use this same connection to send incoming calls
|

|
Phone / VPBX / Connect / Firewall rules[edit | edit source]
| Some customer might complain that the 212.147.44.0/22 is too big, in this case, please use 212.147.47.208/28 instead in the following rules (which is the current Production platform ). This /22 contains all our VoIP infrastructures for Lab + PreProd + Prod, that is why it is so big ( contains 1024 IPs ).
If you wish to know which IP is being used right now by your phones for SIP/SIPS and RTP/SRTP, you need to do a DNS resolution of your SIP domain. It should be right now 212.147.47.217 (for VPBX) or 212.147.47.218 (for ConnectPBX) ( or 212.147.47.215 or 212.147.47.216 for old setup). WARNING, this IPs might change over time, this is why we gave you a wider range. If in the future we change this IP and you setup too narrow rules, your phones won't be able to connect anymore |
| If you own Yealink phones, you will need to allow them to perform NTP queries towards pool.ntp.org which has dynamic IPs ( so allow NTP towards all the internet ), otherwise it won't boot. As a workaround, you could try to redirect NTP queries and have them answered |
- SIP signaling that allows your phone to call out and to receive calls
- IP range: 212.147.44.0/22 (from 212.147.44.0 to 212.147.47.255).
- Port range: UDP/5060 + TCP/5060 + TCP/5061 (for SIP/TLS)
- RTP and RTCP packets that transport the voice and quality call data
- IP range: 212.147.44.0/22 (from 212.147.44.0 to 212.147.47.255)
- Port range: all UDP ports ( WARNING : If you really need a range, use 1024->65535. DO NOT TRY TO GUESS THE PORT RANGE WE ARE USING, IT IS CHANGING OVER TIME WITH CAPACITY INCREASE )
- HTTP/HTTPs for phone auto-configuration
- IP range: secure-provisioning.snom.com + rcs.aastra.com + prov.gigaset.net + profile.gigaset.net + rps.yealink.com + 212.40.12.0/24 + 212.147.44.0/22
- Port range: TCP/80 + TCP/443
- LDAP/LDAPS for Centralized Kiosk Directory
- IP range: 212.40.12.0/24
- Port range: TCP/389 + TCP/636
- DNS/NTP for DNS queries and NTP time updated
- IP range: rs0[1-4].vtx.ch + ( WARNING: Allow "*" in case you own Yealink phones because the Yealink won't boot if there is no answer towards pool.ntp.org which has dynamic IPs )
- Port: UDP/53 + TCP/53 + UDP/123
- Syslog: Used for VTX Support to help debug any problem with auto provisioned phones
- IP range: 212.147.99.16/28
- Port range: UDP/514
NB: Regarding RTP configuration, we do not recommend to set a UDP port range restriction because we can add ranges without notice if needed
Here is an overview of an Tools:iptables configuration
### Allow SIP Signalisation ###
-A FORWARD -p udp -m multiport --dports 5060 -d 212.147.44.0/22 -j ACCEPT
-A FORWARD -p tcp -m multiport --dports 5060,5061 -d 212.147.44.0/22 -j ACCEPT
# Allow all TCP ports for MS Skype for Business
-A FORWARD -p tcp -d 212.147.44.0/22 -j ACCEPT
### Allow RTP (voice) ####
-A FORWARD -p udp -d 212.147.44.0/22 -j ACCEPT
### Allow HTTP/HTTPS ###
-A FORWARD -p tcp -m multiport --dports 80,443 -d secure-provisioning.snom.com,rcs.aastra.com,prov.gigaset.net,profile.gigaset.net,rps.yealink.com,212.40.12.0/24,212.147.44.0/22 -j ACCEPT
### Allow LDAP/LDAPS ###
-A FORWARD -p tcp -m multiport --dports 389,636 -d 212.40.12.0/24 -j ACCEPT
### Allow DNS/NTP ###
-A FORWARD -p udp -m multiport --dports 53,123 -d rs01.vtx.ch,rs02.vtx.ch,rs03.vtx.ch,rs04.vtx.ch -j ACCEPT
-A FORWARD -p tcp -m multiport --dports 53 -d rs01.vtx.ch,rs02.vtx.ch,rs03.vtx.ch,rs04.vtx.ch -j ACCEPT
### Allow all NTP servers for Yealink phones that needs NTP towards pool.ntp.org to work at boot process otherwise they won't boot, and since pool.ntp.org is dynamic, all NTP traffic needs to be allowed ###
-A FORWARD -p udp -m multiport --dports 123 -j ACCEPT
### Allow Syslog ###
-A FORWARD -p tcp -m multiport --dports 514 -d 212.147.99.16/28 -j ACCEPT
-A FORWARD -p udp -m multiport --dports 514 -d 212.147.99.16/28 -j ACCEPT
Teams Connect/Virtual Firewall Rules[edit | edit source]
| We have enabled Media Bypass to have the Secured RTP traffic going directly from the Teams Phone to VTX SBC without going via the Microsoft Teams Cloud to reduce call latency. So if you have restrictions on your firewall, you also need to allow VTX Specific IPs |
- SIP Signaling: Here are the FQDN to use to define the destination of the trunk
- sip.pstnhub.microsoft.com – Global FQDN – must be tried first.
- sip2.pstnhub.microsoft.com – Secondary FQDN – geographically maps to the second priority region.
- sip3.pstnhub.microsoft.com – Tertiary FQDN – geographically maps to the third priority region.
- SIP/TLS Firewalling: The SIP/TLS flows could come from one of these IPs and TCP Range
- IP Range: 52.114.148.0 + 52.114.132.46 + 52.114.75.24 + 52.114.76.76 + 52.114.7.24 + 52.114.14.70
- SIP/TLS Source Port Range: 1024 – 65535
- RTP Transport Relay Firewalling: The media traffic flows to and from a separate service in the Microsoft Cloud. The IP range for Media traffic:
- RTP IP Range: 52.112.0.0 /14 (IP addresses from 52.112.0.1 to 52.115.255.254).
- UDP/SRTP Source Port Range : 49152 – 53247
- RTP Media Bypass Firewalling: This is used for Media Bypass
- RTP IP Range: 52.112.0.0 /14 (IP addresses from 52.112.0.1 to 52.115.255.254).
- UDP/SRTP Source Port Range : 50000 – 59999
- VTX RTP Media Bypass Range: This is used by VTX SBCs
- RTP IP Range: 212.147.44.0/22 (IP addresses from 212.147.44.0 to 212.147.47.255).
- UDP/SRTP Source Port Range : 10000 - 39999
| By default, outgoing billed calls are only possible from a Switzerland IP, this change be changed to Europe/World or ACL from a Kiosk Admin account, see "Outgoing Calls" below |
Here are the different GeoIP restrictions on the Telephony platform
- Physical phone auto provisioning: is only working from Switzerland and France ( other location could be added on request )
- VTX Softphones : Could be used anywhere in the world ( but you still need to allow outgoing calls if calling from abroad, cf below )
- Register and Incoming Calls: Open to the whole world
- Outgoing Calls: Billed outgoing calls are only allowed from Switzerland by default ( This setting can be changed from customer Admin Kiosk interface to open it to Europe or World or some specific IPs) (@VTX: Please refer to Network:Firewall:Configuration#GeoIP_Filtering for more details)
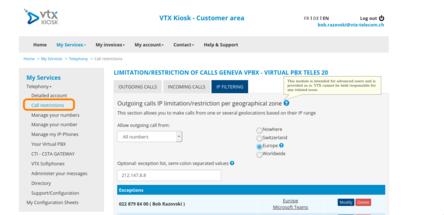
- These settings can be found under "My Services - Telephony - Call restrictions - IP Filtering"
- The "IP Filtering" tab is only visible if you access the kiosk from a swiss IP address (otherwise this tab is hidden)
- A customer can't do any adjustments if he is already abroad. In such case these changes would have to be done by someone who has access from an IP in Switzerland, or uses TeamViewer / Remote access / VPN / proxy server for the modification.
Other Network Restrictions[edit | edit source]
| Some firewalls or remote ISP might also restrict VoIP, you can use the following tests to verify connectivity |
- Ping the VoIP platform which is opened to ping from the whole world
ping s1.12345.bus.ipvoip.ch
PING vtx.res.ipvoip.ch (212.147.47.217) 56(84) bytes of data.
64 bytes from fix.47.147.212.vtx.ch (212.147.47.217): icmp_seq=1 ttl=53 time=7.65 ms
64 bytes from fix.47.147.212.vtx.ch (212.147.47.217): icmp_seq=2 ttl=53 time=8.32 ms
64 bytes from fix.47.147.212.vtx.ch (212.147.47.217): icmp_seq=3 ttl=53 time=8.14 ms
--- s1.12345.bus.ipvoip.ch ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2002ms
rtt min/avg/max/mdev = 7.659/8.041/8.324/0.289 ms
- SIP is also allowed to work on TCP, so you can use telnet to verify your connectivity towards the platform (you need to see "connected" message)
telnet s1.12345.bus.ipvoip.ch 5060
Trying 212.147.47.217...
Connected to s1.12345.bus.ipvoip.ch.
Escape character is '^]'.
Sonicwall VoiP Configuration[edit | edit source]

|
Please do not forget to enable Consistant NAT on the Sonicwall, we have noticed bugs on Sonicwall with Downstream audio problem after some time when disabled !
|

|
You can find here the VoiP parameters for the sonicwall validate by VTX.
- Modifications to perform on the Sonicwall
- VoIP / Settings / Enable Consistant NAT => Sonicwall Doc Helper
- On the WAN interface, please set "Do not send ICMP Fragmentation Needed for outbound packets over the Interface MTU"
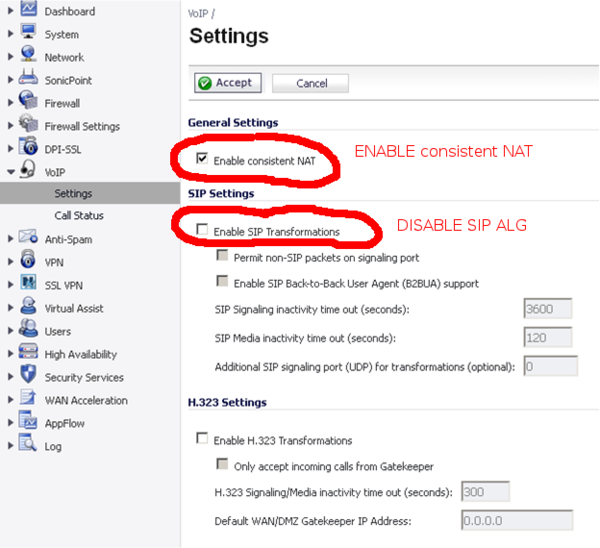 Sonicwall - Disable SIP ALG |
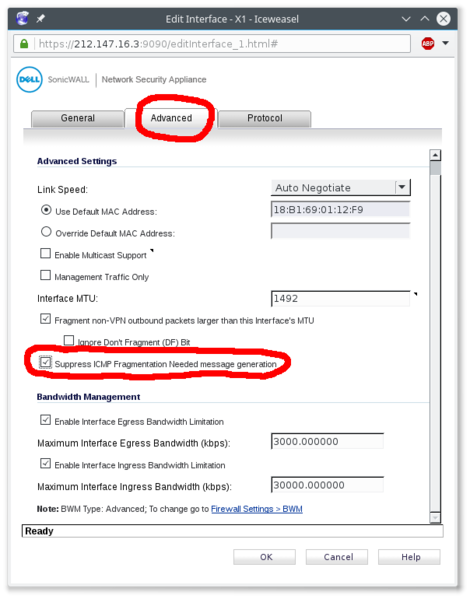 Sonicwall - Suppress ICMP Fragmentation Needed message generation if Sonicwall is doing PPPoE with MTU 1492 |
| On Watchguard, if used together with Snom, possible call cut and audio problemes - Watchguard should get updated to Firmware: 12.1.3.B563398 (Fireware OS) |
Connection UPC / check Modem[edit | edit source]




